Ezra Zigmond
I received a bachelor's degree in Computer Science from Harvard in 2018 where I wrote a thesis on language-based database security with Prof. Stephen Chong and was a Head Teaching Fellow for CS51, one of the largest courses at Harvard.






Contributed to the group's research on developing intelligent information sharing algorithms for supporting distributed teamwork.

Hyland creates enterprise content management software to help businesses manage documents, information, and everyday tasks. I worked on the image upload functionality of OnBase for iPad.

DARMC is a digital humanities project at Harvard that publishes freely available maps and geodatabases created from historical data on Roman and medieval civilization. A common task in the project was manually looking up and filling in coordinates for large CSV files of historical place names. I improved on an existing effort to automate this process.
Database-backed applications often run queries with more authority than necessary. Since programs can access more data than they legitimately need, flaws in security checks at the application level can enable malicious or buggy code to view or modify data in violation of intended access control policies. Although database management systems provide tools for controlling access to data, these tools are not well-suited for modern web applications which often have many users and consist of many different software components. First, databases are unaware of application users, and creating a new database user for each application user is impractical for applications with many users. Second, different components of the same application require different levels of database access, which would require creating different database users for different software components. Thus, it is difficult to properly limit the authority an application has when executing queries.
I propose ShillDB, a language for writing secure, database-backed applications. ShillDB enables reasoning about database access at the language level through capabilities, which limit what database tables a program can access, and contracts, which limit what operations a program can perform on those tables. ShillDB contracts are expressed as part of function interfaces, making it easy to specify different access control policies for different components of an application. These contracts act as executable security documentation for consumers of ShillDB programs and are enforced by the language runtime. Further, ShillDB provides database access control guarantees independent of the security mechanisms of the underlying database management system.
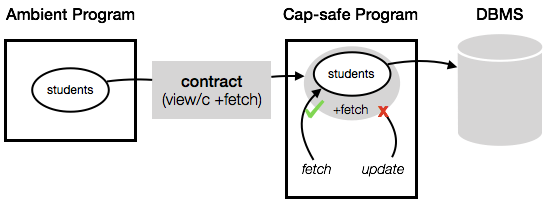
A final project for Advanced Topics in Programming Languages at Harvard.
Users of relational databases often have trouble constructing SQL queries to perform their desired tasks. However, users are often able to provide input-output examples that provide a partial specification for their desired outcome. Accordingly, prior work has developed programming-by-example systems to help users craft database SELECT queries. A natural and useful extension of this technique is to automatically synthesize queries that modify data (that is, UPDATE and DELETE queries), as even users who are proficient in writing SELECT queries may struggle to write these modification queries.
In this paper, we present the first system for synthesizing SQL data modification queries from input-output examples. Our key insight is that it is possible to solve SQL data modification query synthesis problems by issuing multiple, independent calls to an existing SELECT synthesizer, which we can treat as a black box. This results in a simple synthesis algorithm that will benefit from future advances in SELECT synthesis technology. We have implemented our algorithm in a new tool called REAPER which can solve a variety of interesting update problems in a few seconds.
A final project for Projects and Close Readings in Software Systems: Verified Systems at Harvard.
Techniques from language-based security, such as security type systems, often provide protection against high-level adversaries but cannot guarantee security against low-level attackers, such as those that can inject code or inspect memory.We model in Coq a security-typed calculus that includes an abstract model of Intel SGX-like enclaves, and show that the calculus provides meaningful security guarantees, even in the face of low-level attackers. We also model a translation scheme from an enclave-agnostic calculus to an enclave-aware calculus and show that the scheme ensures that enclaves are correctly placed, so that a translation of a well-typed program in the enclave-agnostic calculus results in a well-typed program in the enclave-aware calculus.
A final project for System Security at Harvard.
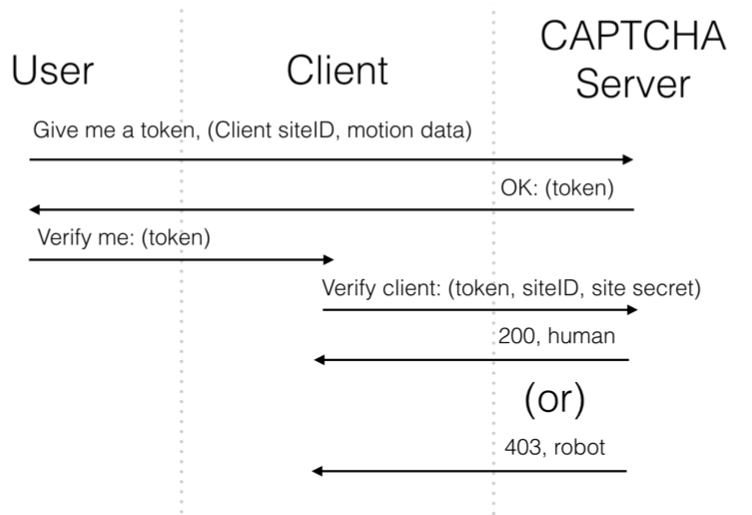
To prevent automated systems from accessing certain webpages, website developers often wish to verify that a user is a human. This generally involves asking a user to perform tasks that are relatively easy for humans but difficult for automated systems. One of the most popular such methods is CAPTCHA. However, these tasks can still be difficult or unpleasant to complete for humans. In general, they can reduce the quality of user experience, which may make a user frustrated when interacting with a system, particularly for those with disabilities.
To address these issues, we explore a replacement for CAPTCHA that uses a mobile client’s accelerometer data to determine whether the client is an automated system. We also examine the privacy implications of websites clandestinely collecting accelerometer data.
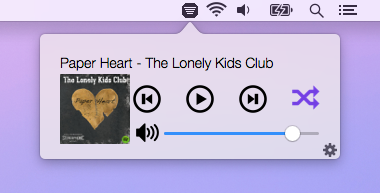
Amplify is a convenient menu bar app to simplify the way you use Spotify. Amplify makes it easy to check the current track, adjust Spotify volume, and control playback without interrupting what you're working on. Amplify has been downloaded more than 75,000 times, peaking at the #4 free music app and the #53 free app overall on the Mac App Store.
Amplify is written in Objective-C and uses the Scripting Bridge Framework to send Apple Script commands to the Spotify client, and the Distributed Notification Center to detect when the Spotify track changes.
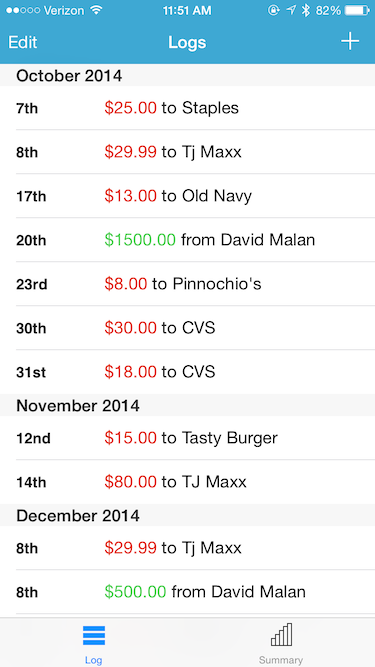
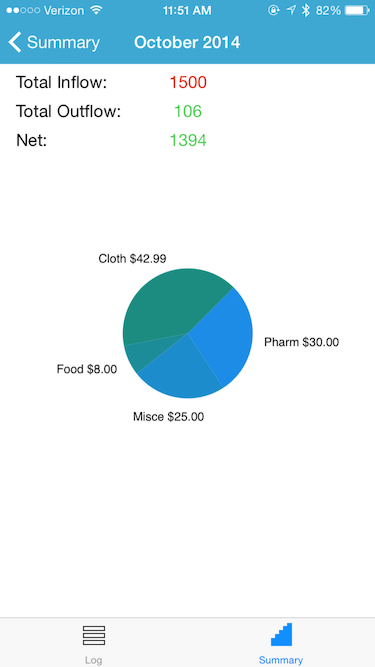
A polite app to streamline your budget management experience. Budget Butler is designed to simplify keeping track of receipts and spending by making it easy to add new receipts as you get them and to view past spending in table or chart form.
Adding a picture of a new receipt automatically fills in the total amount using optical character recognition (OCR) powered by Tesseract. Receipt pictures and information are then saved using Core Data. Budget Butler will even autocomplete payee names and expense categories based on previous saved purchases. In addition to the table-style log, the summary view generates charts using Core Plot to break down spending by category.
A sliding tile puzzle solver written in Clojure as a final project for CS51: Abstraction and Design. The goal of the project was to compare the effectiveness of a standard A* strategy with a genetic algorithm. After running tests on both square and non-square puzzles, we found our A* implementation about 30 times faster than the genetic algorithm. We also compared the effectiveness of different heuristic functions for maximizing the speed of both algorithms, as well as for increasing the accuracy of the genetic algorithm. Ultimately, we concluded that a genetic algorithm was not well suited for a problem of this sort which involves planning and where partial solutions are not useful.


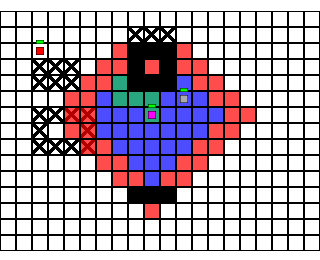
A prototype based on the style of movement found in turn-based strategy games like Fire Emblem and Advance Wars. Determines valid movement ranges and paths based on a character's movement range and finds paths to tiles using a modified depth-limited breadth-first search. Built using Phaser.js to draw grid and animate movement.
To try out the demo, click on and move the pink or the green friendly sprites to a valid (blue-highlighted) tile in movement range. Once you've moved both friendly sprites, the red enemy will make a move. Spaces marked with x's indicate difficult terrain that costs double to cross. The red-highlighted squares indicate spaces within the sprite's "attack" range but outside of its move range.
A game about tiles. Flip is based on a simple goal (turn all of the red tiles white) and a simple mechanic (flipping over a tile also flips the adjacent tiles). Built using Phaser.js.
There are currently two different modes:
